
If you’ve ever built an app on Bubble.io, you’ve probably had that late-night thought:
“What if someone breaks in and steals my users’ data?”
It’s the kind of worry that keeps developers, founders, and even AI-powered app builders staring at the ceiling at 2 AM. And it’s not just paranoia. Once your app is live, the responsibility for protecting that data is on you, not Bubble, not AWS, not “the internet.”
The reality is, Bubble.io can be extremely secure if you take the right steps. Security isn’t something you can “tick off” before launch. It’s an ongoing responsibility.
In this guide, we’ll dive into the three key layers of Bubble.io security you should focus on in 2025:

We’ll also cover how privacy rules, admin controls, and workflows determine exactly who sees what, and how you can make sure you’re not accidentally leaving any gaps.
Think of your Bubble app as a building. The first thing you need to lock is the front door, your user authentication. If this isn’t solid, it doesn’t matter how good your other security measures are.
Your best tool here is Multi-Factor Authentication (MFA). With MFA, even if a hacker gets someone’s password, they still need a second step like a code sent to their phone, an authenticator app, or another trusted device. This one change can block up to 99% of unauthorized login attempts. Strong authentication isn’t just for banks — your app’s users deserve the same level of trust and protection. At InceptMVP, our FinTech-grade authentication solutions make it easy to lock out bad actors while keeping the experience smooth for real users.
But don’t stop there:
Example: Imagine you’re building an internal HR app for your company. Without RBAC, a regular employee might see salary data meant only for HR. That’s not just a privacy issue, it could be a legal one.
Locking this front door early means your app isn’t just closed to strangers it’s reinforced and under constant watch.
A strong door is good, but what about the windows, side entrances, and safes? That’s where data-level security comes in.
On Bubble, your strongest defense here is privacy rules, server-side conditions that decide, for every request, who can view, edit, search, or delete data.
Here’s why privacy rules matter:
As the app creator, you control how data flows through your app.
Only the admin can grant access to specific details.
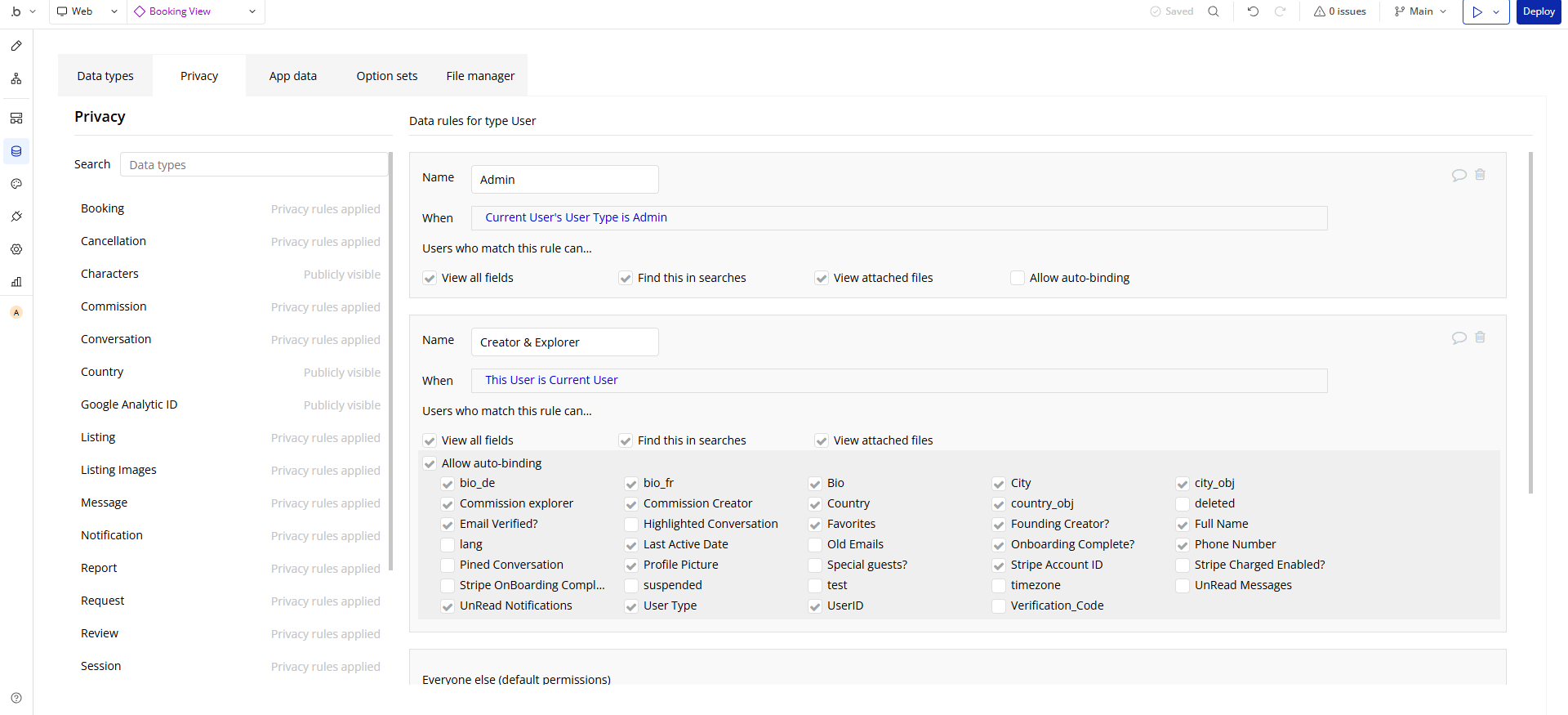
For example, if you’re running a booking platform, your workflow might let a customer see their own booking details but never another customer’s. Even if someone tries to manipulate URLs or run a custom search, Bubble will block them if your privacy rules are set correctly.
How to strengthen this layer:
Compliance-wise, Bubble is SOC 2 Type II and GDPR-ready. But compliance does not equal security. A misconfigured privacy rule can undo all that protection in seconds.
This is the vigilance layer. Threats evolve. Plugins get old. Bugs surface. Staying secure means staying proactive.
Your ongoing security checklist should include:
Example: If you use a payment gateway plugin and forget to update it, you might miss a critical security patch, leaving your app and your customers’ financial data at risk.

The short answer: Yes, if you do your part.
Bubble has the infrastructure, encryption, and compliance covered. But it can’t protect you from your own misconfigurations or bad security habits.
Key takeaways for 2025:
In 2025, Bubble.io security isn’t just a technical feature; it’s part of your brand. You can’t bolt it on later like a new widget. By the time you realize you need it, it’s often too late.
When you bake security into your app from the first click secure authentication, tight data rules, and ongoing system checks, you’re not just following best practices. You’re protecting real people who trust you with their information.
A visually stunning app might grab attention. A secure one earns loyalty. Your users may never see the privacy rules you’ve set or the encryption you’ve enabled, but they’ll feel the peace of mind every time they log in without worry.
.webp)
Discover why Replit is the fastest way to build, test, and deploy real software in 2026 while maintaining full code ownership and scalability.
Read More
Compare Replit vs Bubble vs Lovable to understand which platform offers better scalability, flexibility, and code ownership for modern startups.
Read More.webp)
Learn how founders leverage Replit for AI-powered MVPs and automation tools, building faster, smarter, and scalable products in 2026.
Read More